In today’s interconnected industrial landscape, the convergence of cybersecurity and regulatory compliance has become a critical focal point for organizations operating critical infrastructure. As digital transformation accelerates across industrial sectors, the protection of operational technology (OT) systems has never been more crucial
According to a recent survey, 72% of organizations in operational technology sectors reported experiencing a cybersecurity incident in 2024, highlighting the urgent need for robust security frameworks. This statistic underscores why both cybersecurity measures and compliance requirements must work hand-in-hand to safeguard the systems.
Understanding the OT Compliance Landscape in 2024
The regulatory environment governing operational technology has evolved significantly in recent years, with new frameworks emerging to address the unique challenges of industrial control systems.
Evolution of Critical Infrastructure Protection Standards
Critical infrastructure protection standards have transformed from voluntary guidelines to mandatory requirements in many sectors. Originally focused primarily on physical security, these standards now encompass comprehensive cybersecurity controls. The development of these standards reflects increasing awareness of digital threats to industrial systems.
Organizations working with critical infrastructure must navigate various regulatory frameworks, including IEC 62443 for industrial automation and control systems, NIST 800-823 for industrial control systems security, and the recently strengthened NIS2 Directives in Europe. The NERC CIP standards specifically target the electric power industry, establishing strict requirements for identifying and protecting critical cyber assets.
Industry-Specific Compliance Requirements
Different sectors face unique compliance challenges based on their operational environments and risk profiles. Manufacturing facilities must balance production efficiency with security controls that often weren’t considered when legacy systems were installed.
The energy sector operates under particularly stringent regulations, with electric utilities required to adhere to nerc cip standards that mandate specific protections for bulk electric systems. Oil and gas operators face similar requirements, often adapting electrical sector practices to their operational context.
Transportation, healthcare, and water treatment facilities each have their regulatory frameworks, creating a complex patchwork of compliance requirements that organizations must navigate while maintaining operational continuity.
The Real Cost of Non-Compliance
The consequences of failing to meet compliance requirements extend far beyond regulatory fines. Financial penalties for critical infrastructure protection violations can reach millions of dollars, particularly in heavily regulated sectors like electric utilities.
Beyond immediate financial impacts, operational disruptions resulting from compliance failures can lead to service interruptions, production losses, and safety incidents. The Texas power outages of 2021 highlight how inadequate preparation and compliance can have catastrophic consequences.
Perhaps most damaging is the reputational impact when organizations fail to protect critical systems. The erosion of stakeholder trust can have lasting effects on an organization’s ability to operate effectively.
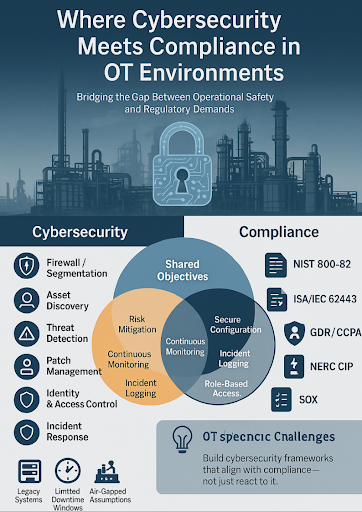
The Gap Between Traditional IT and OT Security Compliance
Understanding the fundamental differences between information technology and operational technology environments is crucial for effective security and compliance. These differences shape how organizations must approach protection strategies.
IT vs. OT: Fundamental Differences in Security Priorities
Traditional IT systems prioritize data confidentiality above all else, while OT environments place availability and system integrity at the forefront. This fundamental difference drives many security decisions and compromise calculations.
Legacy systems with decades-long lifecycles create unique challenges in OT environments. Unlike IT systems that refresh every 3-5 years, industrial control systems often operate for 15-30 years, making traditional patching and update cycles impractical.
The physical impact potential of OT security failures introduces safety considerations rarely present in IT environments. When a breach can cause equipment damage or endanger human lives, security approaches must evolve accordingly.
Common Compliance Pitfalls in Converged Environments
Many organizations stumble by applying IT-centric solutions to operational technology problems. Security measures that might be standard in corporate networks can disrupt critical processes in industrial environments.
Over-reliance on network segmentation and perimeter security often creates a false sense of security. While essential, these measures must be complemented by defense-in-depth strategies designed specifically for OT vulnerability management.
Communication gaps between security teams and operational personnel frequently undermine compliance efforts. When security requirements are implemented without operational input, they often create unintended consequences that can impact reliability.
Bridging the IT/OT Divide
Cross-functional teams with representation from both security and operations provide the foundation for effective governance. These teams ensure security measures align with operational requirements.
Tailored policies that acknowledge the unique constraints of operational technology environments help organizations maintain compliance without compromising safety or reliability. The most successful programs adapt IT security principles rather than adopting them unchanged.
Technology solutions designed specifically for industrial environments can accommodate the performance requirements of both worlds. These specialized tools support OT vulnerability management while respecting the operational constraints of industrial systems.
Essential Components of an OT Compliance Strategy
Building an effective OT compliance strategy requires a structured approach that addresses the unique challenges of industrial environments. These components form the foundation for sustainable compliance programs.
Asset Inventory and Classification in OT Networks
Comprehensive visibility across industrial control systems represents the foundation of any effective compliance program. You can’t protect what you don’t know exists, making accurate inventory essential.
Risk-based approaches to asset classification help organizations prioritize protection measures where they matter most. Not all systems require the same level of protection, and effective classification helps allocate limited resources.
Automated discovery tools designed for OT environments can provide continuous monitoring without disrupting operations. These specialized tools respect the sensitivity of industrial protocols and avoid active scanning that might impact control systems.
OT Vulnerability Management Best Practices
Identifying vulnerabilities in operational environments requires specialized approaches that don’t disrupt production processes. Passive monitoring techniques and scheduled assessments during maintenance windows help minimize operational impact.
Prioritization methodologies that consider both technical vulnerability severity and operational context enable effective remediation planning. The critical infrastructure protection context demands that remediation decisions balance security, operational, and safety considerations.
Compensating controls play a crucial role when patching isn’t possible. Many legacy systems cannot be patched due to vendor constraints or operational requirements, making alternative protection measures essential.
Documentation and Evidence Collection for Audits
Building auditable records throughout the compliance process simplifies regulatory reporting and demonstrates due diligence. Comprehensive documentation should track vulnerability identification, risk assessment, and remediation activities.
Automation of compliance documentation reduces the burden on operational teams while improving accuracy. Specialized platforms can track compliance activities and generate reports aligned with specific regulatory requirements.
Creating defensible evidence of due diligence protects organizations during regulatory review. Even when perfect compliance isn’t achievable, documented risk acceptance and compensating controls demonstrate good-faith effort.
With these foundational compliance elements established, let’s examine how electric utility practices can inform protection strategies across all critical infrastructure sectors.
Moving Beyond Checkbox Compliance
Looking beyond mere regulatory compliance, effective OT security requires a comprehensive approach that integrates with an organization’s broader risk management strategy. The most successful organizations view compliance not as a destination but as a continuous journey toward improved security maturity.
As digital transformation continues to reshape industrial operations, the integration of effective security practices with compliance requirements will only grow in importance. Those organizations that bridge the gap between security and compliance will be best positioned to protect their critical systems from evolving threats while maintaining regulatory standing.
By focusing on continuous improvement rather than checkbox compliance, organizations can build resilient operational technology environments that support their functions while protecting against increasingly sophisticated cyber threats.
Common Questions About Critical Infrastructure Cybersecurity
What is the OT environment in cyber security?
Operational Technology (OT) cybersecurity focuses on protecting the uptime, security and safety of industrial environments and critical infrastructure. It addresses the unique challenges of systems that control physical processes rather than just information.
What is the cybersecurity framework for OT?
The OT CSF builds upon the NIST Cybersecurity Framework and NIST 800-82. NIST CSF provides a comprehensive approach for improving information security and risk management, while NIST 800-82 offers extensive guidance specifically for securing operational technology environments.
How do you ensure cyber security compliance?
Businesses ensure cybersecurity compliance by first understanding applicable regulations based on their industry and data types. They must conduct risk assessments, implement required security controls, establish policies, and continuously monitor their environment for emerging threats and vulnerabilities.









